Iptables is a firewall service included in CentOS, in CentOS 7 its offered as a alternative firewalld is offered as well. Iptables uses netfilter to filter chains. Essentially you create a chain of filter rules to process how incoming and outgoing data is handled. You can view more about iptables on Netfilter
Iptables rule format
The iptables rules format is pretty simplistic when using basic rules to allow or deny traffic.
iptables -t <type> <direction> <pattern> -j <action>
Type
for -t <type> there are two basic type options filter and nat
filter – creates a rule for filtering traffic.
nat – this creates a nat(network address translation) rule.
Direction
–append – Adds a rule to the end of the chain. You also want to specify INPUT (incoming packets) or OUTPUT (outgoing packets) when appending rules.
–delete – Deletes a rule from the chain. You also want to specify INPUT (incoming packets) or OUTPUT (outgoing packets) when deleting rules.
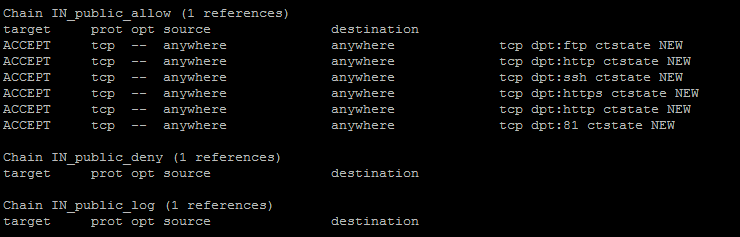
–list – lists the current rules
–flush – flushes all the rules
Pattern
–source <ip_address> – Rule only applies to packets coming from this source IP address.
–destination <ip_address> – Rule only applies for packets going to this destination IP address.
Action
DROP – packets are dropped
REJECT – packets are dropped and a error message sent back
ACCEPT – packets are allowed
Iptables Service Management
How to manage the IPtables service itself.
To start iptables:
service iptables start
To stop iptables:
service iptables stop
To ensure iptables starts on reboot:
CentOS 6:
chkconfig --add iptables
chkconfig iptables on
Centos 7:
systemctl enable iptables
Restore saved ruleset:
iptables-restore < /etc/sysconfig/iptables
Save new rules permamently:
iptables-save > /etc/sysconfig/iptables
Example rules:
Samples of different functions you can perform to block or accept traffic based on IP addresses and Ports.
Block a IP with Iptables:
iptables -A INPUT -s 1.2.3.4 -j DROP
Allow a IP
iptables -A INPUT -s 1.2.3.4 -j ACCEPT
Block a PORT:
iptables -A INPUT -p tcp --dport 21 -j DROP
Allow a IP to a specific port:
iptables -A INPUT -s 1.2.3.4 -p tcp --dport 21 -j ACCEPT
There is much more that you can do with iptables this is just a basic introduction.