ModSecurity is an open source monitoring system for web applications. It has powerful rule sets that allow you to protect applications from attacks. View the project for more details. It provides a ton of features such as:
More than 16,000 specific rules, broken out into the following attack categories:
* SQL injection
* Cross-site Scripting (XSS)
* Local File Include
* Remote File Include
User option for application specific rules, covering the same vulnerability classes for applications such as:
* WordPress
* cPanel
* osCommerce
* Joomla
Install ModSecurity
To get started you will need to have Apache installed. If you do not yet, please see Compile Apache 2.4 From Source
Install the required dependencies:
yum install -y libxml libxml-devel
Get the software package:
cd /usr/src; wget https://github.com/SpiderLabs/ModSecurity/releases/download/v2.9.1/modsecurity-2.9.1.tar.gz
Un-compress the archive:
tar xfvz modsecurity-2.9.1.tar.gz
Go in to the directory:
cd modsecurity-2.9.1
Configure it:
./configure
Install:
make && make install
You will need to edit /etc/httpd/conf/httpd.conf and load the module:
LoadModule security2_module lib/apache/mod_security2.so
For each domain you want to enable it for add the following:
SecEngine On
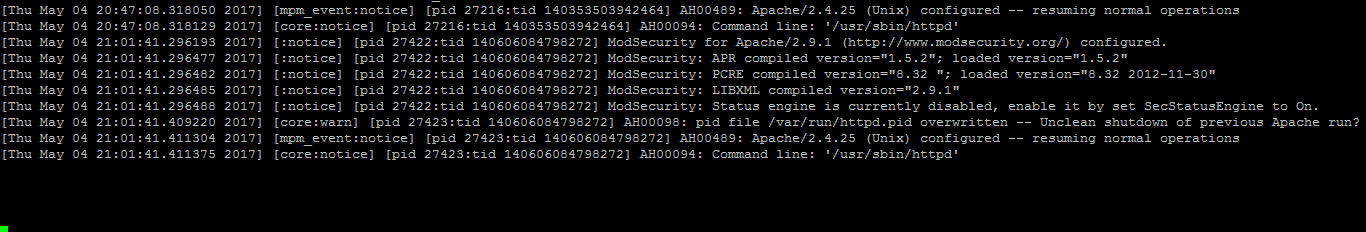
Restart Apache to load it:
service httpd restart
Verify it is loading in Apache:
httpd -M 2>&1|grep security
You should see the following returned:
security2_module (shared)
Configure ModSecurity
Get a starting ruleset. View the github project for more details.
Download the ruleset:
cd /usr/src;wget https://github.com/SpiderLabs/owasp-modsecurity-crs/archive/v3.0.0.tar.gz
Un-compress the archive:
tar xfvz v3.0.0.tar.gz
Make a configuration directory
mkdir /etc/httpd/conf/modsecurity.d
Enter the directory:
cd owasp-modsecurity-crs-3.0.0
Move the rules directory into place:
mv rules/ /etc/httpd/conf/modsecurity.d
Move and rename the main configuration:
mv crs-setup.conf.example /etc/httpd/conf/modsecurity.d/crs-setup.conf
Review crs-setup.conf and remove comments for any applicable lines.
Edit /etc/httpd/conf/httpd.conf once again and add the following:
<IfModule security2_module> Include /etc/httpd/conf/modsecurity.d/crs-setup.conf Include /etc/httpd/conf/modsecurity.d/rules/*.conf </IfModule>
Restart Apache once more to load the base configuration. That is it for the base installation. There are numerous ways you can configure it to protect your server from web based attacks and proactively monitor your server.

Thanks, great article.